APK Reversing
Let's discuss one of the most important skills - reversing Android applications. Reversing allows us to get a complete view of the built application, including all libraries and the impact of the building process.
What is reversing?
It's the process of transforming a compiled application back to something resembling the source code. It allows us to look for hard coded secrets, review the code for vulnerabilities and understand how the application works.
Tools?
Here are some common tools used and I highly recommend installing them on your testing machine/VM:
jadx-gui
apktool
jd-gui
smali
dex2jar
baksmali
Android Studio
There are a gazillion write-ups on how to setup Android Studio, jadx-gui and apktool so get set up! Ideally, you'd want to have a dedicated laptop + a physical device but we can make do with a VM (Ubuntu or w/e) and an emulator via Android Studio. For some reason, if your setup can't handle the emulated device there is also the Android x86 emulator VM you can download and run on your hypervisor to help with this.
Obfuscation
Obfuscation is the process of intentionally making the code harder to read for the purpose of making it harder to reverse.
Typically, developers will do this to protect their IP but sometimes it also helps with optimization such as minifying. It's a generic term to reduce size of the code and improve performance and reduce app size.
It makes it harder but not impossible. A determined reverser can still reverse the app given enough time.
You can use something like ProGuard in Android Studio to help with basic obfuscation.
Hardware Optimization
Sometimes when we reverse an APK, we find there is no classes.dex . If it comes installed on your device then it likely has an .odex file. The odex format is used to speed up the first boot of a ROM.
If you would like to prevent the classes.dex file from being disassembled, you can specify the -s flag using apktool.
Jadx-GUI in action
Here we look at a few screenshots of the JADX-GUI tool in action.
- Here is the navigation pane showing us the usual suspects such as the highlighted
AndroidManifest.xmland more.
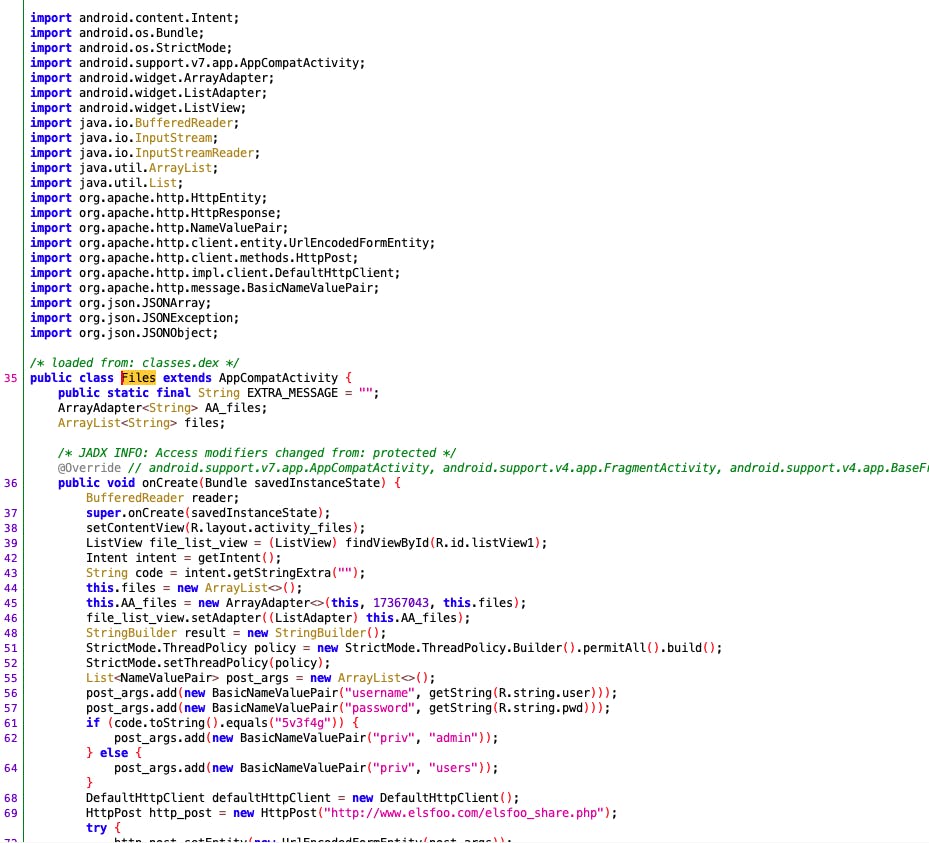
- A look at decompiled source code
ADB
Before we end this post, let's have a quick chat about Android Debug Bridge or adb which is going to be an important tool we use throughout the Android world.
This provides access to a Unix shell that we can use to communicate with the device. It is a client-server program which uses
Client
Daemon -
adbdServer
When we start an adb client, it checks if there is an adb server running. If it isn't, it'll start one for us. It binds itself to the local port 5037 (TCP) and listens for any incoming communications from clients.
Following this, it starts scanning for all running devices on odd numbered ports ranging from 5555 to 5585. When it finds one running it sets up a connection to that port. Once the server has set up the connection we can send commands to access those devices.
That's all folks! I know this was a short post but get ready for the next one, it's going to be a long one. We will take a deeper dive into the Android app structure.

